Complexity of compliance
Implementing a regulatory compliance policy

To ensure your company's compliance, it's crucial to implement a regulatory compliance policy. Here are the key steps to follow:
Learn about and understand regulatory obligations
It is essential for any business to have a clear understanding of the regulatory requirements for combating terrorist financing and money laundering. Define a clear policy to implement the appropriate measures.
Adapting internal organization
Appoint a compliance manager and department reporting directly to senior management. This ensures proper supervision and clear responsibility within the company.Adapting processes
Update your processes to incorporate regulatory constraints, particularly with regard to Know Your Customer(KYC), due diligence and money laundering risk assessment.
Equip yourself with IT tools
Invest in high-performance IT tools and integrate them into your screening tools such as CRM or KYC. These tools must make it possible to identify sanctioned or politically exposed individuals, and to keep proof of the checks carried out.
- Staff training Make sure your staff is well trained in new processes and compliance tools. Ongoing training is essential to maintain a high level of compliance.


Your practical obligations
o meet regulatory compliance requirements, companies must :
- Identify all third parties involved in their business activities (customers, prospects, co-owners, signatories, legal representatives, subscribers, beneficiaries).
- Keep proof of identification (ID cards, passports, etc.).
- Check the identity of third parties against national, European and international sanction lists.
- Identify Politically Exposed Persons (PEP).
- Customer due diligence.
- Assess the risk of money laundering.
- Determine level of vigilance.
- Keep proof of due diligence.
- Report any suspicions
Supervisory and control bodies
Regulatory compliance is overseen by a number of supervisory and control bodies:
- The Financial Action Task Force (FATF) and its Financial Action Task Force (FAFT) lead the global effort to combat money laundering and the financing of terrorism, hosted in France.
- The European Anti-Money Laundering Authority (AMLA)soon to be based in Paris, will reinforce the monitoring system.
- The Autorité de Contrôle Prudentiel et de Résolution (ACPR) supervises the banking and insurance sectors, and is a benchmark for regulatory compliance AML-CFT.
- The Autorité des Marchés Financiers (AMF) gives priority to the fight against money laundering and the financing of terrorism.
- The DGCCRF monitors sectors such as real estate to combat money laundering and the financing of terrorism.
- The Treasury Department and Tracfin act on money laundering and facilitate the reporting of suspicions.
- The French Anti-Corruption Agency (AFA) monitors the effectiveness of anti-corruption measures
Importance of regulatory compliance
The fight against financial crime (AML-CFT) has become a major challenge for companies. International regulations require companies to set up compliance programs to combat money laundering and the financing of terrorism. In the event of non-compliance, fines can be very high, and executives can be held criminally liable.
To protect your business, regulatory compliance is essential. Our regulatory compliance solutions can help you secure your business and avoid the risks of non-compliance. Contact us today to find out how our solutions can meet your specific needs and ensure your peace of mind.
By integrating these practices, you'll ensure your company's compliance and contribute to a safer, more stable business environment.
FAQ
With the Sapin 2 law, France is equipped with innovative tools to effectively detect, prevent and punish corruption and breaches of probity. The law aims to respond to the aspirations of the French people for transparency, ethics and justice in economic matters. "Ethics must be the compass of public and economic life", declared Michel Sapin, for whom "this text will contribute to making our country a modern democracy, based on solid values, and not a democracy of suspicion. It will help build an economy that serves everyone" and eliminate "unbridled finance at the service of corruption and speculation.
List quality: The nature and quality of the databases used to filter sensitive persons (individuals or legal entities) vary. It is necessary to consider the sources from which the information originates, and to question the intrinsic value attached to each piece of information collected. AP solutions IO uses national and global watch and sanction lists from national, international and intergovernmental organizations, as well as from the most reputable private companies. These lists are constantly updated by thousands of analysts worldwide. Assets Freeze Asset freeze The asset freeze is an economic and financial sanction in the fight against terrorism and money laundering. Asset freezes are designed to restrict access to the financial resources of any person committing a breach of the law AML-CFT. In concrete terms, any change in the volume, amount, location, ownership, possession, nature and destination or use of funds or economic resources will be blocked by these measures. The consequences of freezing assets are diverse:
- General or targeted import or export restrictions;
- Restrictions on access to financial markets, prohibitions on granting loans or credit, transferring funds or providing insurance or reinsurance services.
Sanctions Internationales & Embargo Le filtrage des transactions est une obligation LCB-FT visant à vérifier que la transaction du client n’est pas soumise à sanction internationale (contrepartie sous sanction) ou à embargo commercial (restriction d’activité pour certains pays). Naviguer au milieu des règlements, listes, annexes relevant des sanctions et embargos et des juridictions compétentes peut relever d’un vrai parcours du combattant ! L’ensemble des acteurs économiques a vite mesuré l’importance des enjeux associés au non-respect de ces principes. Les amendes, prononcées par les autorités de réglementation se sont en effet multipliées, jusqu’au triste record établi pour un établissement français de 8,9 milliards de dollars à verser au trésor américain pour contournement d’embargo ! L’analyse doit permettre en premier lieu de déterminer si l’opération ou la transaction est susceptible de tomber sous un ou plusieurs régimes de sanctions économiques (sanctions nationales, EU, US et internationales). Elle doit également présenter et évaluer les autres risques associés à la transaction, par exemple le risque réputationnel ou les risques opérationnels directement liés aux flux financiers ou le risque de LCB/FT lié au financement du commerce international. La documentation précise de l’ensemble de l’analyse, des éléments de contexte, et du cadre règlementaire doit absolument être tracée, datée et archivée. Nos solutions vous accompagnent méthodiquement pour gérer, analyser et tracer ces risques. PPE Les Personnes Politiquement Exposées (PPE) sont des personnes qui sont considérées, au niveau international, comme exposées à des « risques plus élevés » de blanchiment de capitaux ou de corruption. Les personnes concernées qui exercent, ou ont cessé d’exercer depuis moins d’un an (nos critères de détection permettent de modifier ce délai), des fonctions politiques, juridictionnelles ou administratives pour le compte de la France, d’un État étranger ou d’une organisation internationale. RCA Relatives and Close Associates. Il s’agit des proches des PPE comme les conjoints, enfants, parents. Les personnes étroitement associées aux PPE, notamment dans le cadre d’une société ou structure juridique (fiducie ou trust) ou entretenant un lien d’affaires (commercial ou économique) étroit. Au-delà de cette définition des régulateurs, et suivant votre appétence au risque, nous pouvons aller plus loin dans la granularité et la complétude de l’information à traiter grâce à la puissance de nos filtres portant sur les relations entre tiers. Adverse MEdia (AME) ou Media Défavorables ou Négative News Le large spectre des infractions liées au blanchiment d’argent oblige, depuis la 6ème directive anti-blanchiment de l’Union Européenne (6AMDL entrée en vigueur fin 2020), d’ajuster le processus de filtrage sur la presse négative pour s’assurer d’une identification correcte des informations de dernière minute sur ses clients ou tiers. Compte tenu du travail important qu’impliquerait ce processus, l’automatisation de la filtration des médias défavorables est un outil indispensable qui permet de trier et hiérarchiser les nouvelles informations médiatiques et d’évaluer dans quelle mesure elles pourraient modifier le profil de risque d’un client ou porter atteinte à la réputation de votre établissement. Bénéficiaire Effectif Le tiers évalué ne se limite pas au tiers « apparent » ou tiers « facial ». La notion de bénéficiaire effectif résulte de la transposition de la 3ème directive LCB-FT et pose les critères de détention de plus de 25 % du capital ou des droits de vote d’une société cliente, et de l’exercice, par tout autre moyen, d’un pouvoir de contrôle sur la société au sens du code de commerce. Ainsi, les organismes assujettis sont tenus d’identifier et de vérifier l’identité du bénéficiaire effectif de leurs clients en relation d’affaires. Les documents recueillis à ce titre doivent être régulièrement actualisés, tout comme pour le client en relation d’affaires. La 4ème directive LCB-FT a permis de préciser la notion de bénéficiaire effectif. A cet égard, la mise en place du registre des bénéficiaires effectifs des sociétés – tenus par les tribunaux de commerce – constitue une aide pour les organismes assujettis sans pour autant exempter ces derniers de leurs obligations d’identification et de vérification de l’identité des bénéficiaires effectifs. Depuis la 5ème Directive il est indiqué qu’une preuve d’enregistrement ou un extrait du registre contenant les informations relatives aux bénéficiaires effectifs devra être recueilli par les organismes assujettis lors de l’entrée en relation avec une personne morale ou une entité concernée par l’obligation d’enregistrement. ORIAS : L’ORIAS immatricule les intermédiaires (personnes morales ou physiques en France) en assurance, opérations de banque et de services de paiement (IOBSP), conseillers en investissements financiers (CIF), agents liés de prestations de services d’investissement (ALPSI), conseillers en financements participatifs (CIP), des intermédiaires en financement participatif (IFP). Nos outils permettent en filtrant ces listes la vérification de la validité du numéro d’Orias, des accréditations obtenues et le contrôle des dates d’expiration de ces mêmes accréditations. INPI : Analyse financière, aide à la décision, statistiques… L’Institut national de la propriété industrielle (INPI) permet de consulter – sous forme de téléchargement – les informations non confidentielles issues des comptes annuels des entreprises commerciales françaises, compilées dans le registre national du commerce et des sociétés (RNCS).
Data INPI: what data is available?
company legal identity data from all commercial court registries, centralized by INPI in the National Trade and Companies Register (RN CS): e.g. date of creation, registration, legal form, share capital, company name, trade name, acronym, principal activity, representatives, Beneficial Owners, and addresses of establishments. These data can also be used to track the life of companies: modifications and deletions, data relating to articles of association and company deeds, as well as non-confidential annual accounts (data on balance sheets, income statements, fixed assets, depreciation and provisions). OPEN DATA: Open Data or "open sources" refers to all activities and methods for disseminating, collecting and analyzing information obtained from a public source, i.e. information available to anyone. These sources include newspapers, websites, books, scientific magazines, radio broadcasts, television programs and so on. In addition, there are many other public databases that have emerged from the general movement to open up public data. Open sources can contain reliable information, but they can also contain information that should be treated with caution: false information, information whose validity is outdated, or whose basis is subjective or biased. This is why AP Solutions IO does not include screening of unverified sources as standard, but can integrate any type of OPEN DATA list you wish, depending on your risk appetite.
A report of suspicion must be made before a transaction is carried out, to enable Tracfin* to exercise its right of opposition. This report must also be made without delay in the event of suspicions arising after the transaction has been carried out. *Tracfin is an intelligence service under the authority of the French Ministry of the Economy, Finance and Industrial and Digital Sovereignty. It contributes to the development of a healthy economy by combating clandestine financial circuits, money laundering and the financing of terrorism. Professionals must therefore refrain from carrying out any transaction they suspect may be linked to money laundering or terrorist financing. There is no legal threshold for reporting suspicious transactions. Tracfin must be informed without delay of any new element that may invalidate, confirm or modify the content of the report. Professionals are obliged to keep all documents gathered as part of their due diligence for a period of 5 years. Without a powerful detection and filtering tool AML-CFT , it is virtually impossible to comply with reporting obligations, even though failure to do so can result in heavy fines and criminal liability for the manager! Measures can be implemented and monitored using our follow-up system. Depending on the due diligence carried out, APScan displays a list of actions to be taken. You can check off the action as it is taken. You now have all the information you need to analyze and make your mandatory declarations to TRACFIN.
A Black Box is any system, device or object capable of being observed in terms of its transfer characteristics (inputs and outputs), without clear knowledge of its intrinsic organization and operation. In contrast, the term Glass Box (transparency) allows for total explicability, as required by regulations. This is AP Solutions IO's choice: 100% compliance, everything is explicable and traceable!
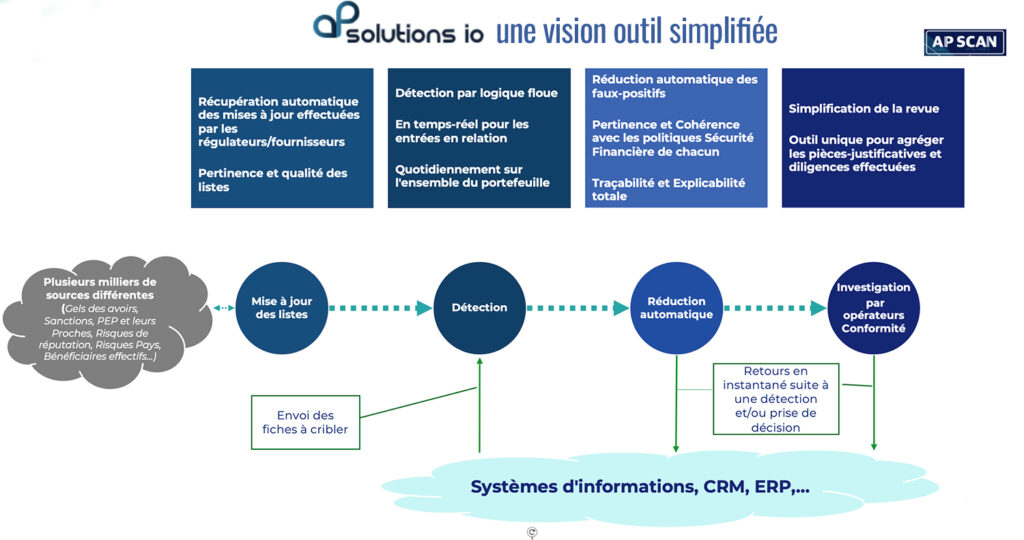
Under the anti-money laundering and combating the financing of terrorism system (AML-CFT), companies must monitor their customers' activities using automatic person and transaction filtering systems, which generate alerts on suspicious persons or financial movements. These alerts are then validated or dismissed by the company's compliance officer. Confirmed suspicious cases are consolidated in the form of a "suspicious transaction report", which must be forwarded to the Treasury Department or the Tracfin financial intelligence unit. The regulations impose fuzzy logic detection, i.e. detection with spelling, graphic or phonetic approximations... This imposed detection typology leads to the generation of numerous suspicions known as " false positives". The more suspicions there are, the more business is slowed down, and the more company operators have to manually review customer files. Our tool for detecting sensitive transactions or persons offers powerful reduction engines. This step consists in eliminating false positives "The result is up to 98% reduction in false positives! It is essential, particularly in the event of a control by a regulatory authority, to be able to explain and demonstrate the reasons for automatic elimination of a suspicion. Finally, all these steps would be in vain if the tool were not connected to the information system, CRM, ERP... of the companies and subsidiaries with this detection need.
After filtering, a transaction may generate an alert on a person or entity in false positive. To avoid this same alert being generated the next time a similar transaction is filtered, we can create a " Good Guy " mechanism. If there is an alert with no impact, the Good Guy joker closes the alert. Good Guys are maintained in the form of a list, with applicability statistics, an expiry date and under the strict control of Compliance Officers. A regulator auditing the system would request both the Good Guy lists and, above all, the organizational process surrounding Good Guy management. The Bad Guy is, by contrast, the listed entity that has matched part of the transaction. These are the individuals or entities that are simply present in the lists. This ultra-simple practice is taught to you during the commissioning of your tools.
APScan has prepared the ground for risk classification by breaking down several key stages in the process and treatment of detecting sensitive persons:
- Alert generation
- Qualification of whether the alert is TRUE or FALSE (called a False Positive)
- Third-party due diligence (generally results from the qualification of alerts) :
- Establishing a risk level
- Define the category of Third Party (SCT, PEP, AME...)
- Customer decision: ACCEPT (+ level of vigilance), REFUSE
These steps enable fine granularity in the processing carried out vis-à-vis a Third Party. APScan goes even further with a profiling system that enables you to automate part of the risk classification process, based on fully configurable scoring rules.
APScan traces all user and system actions, providing a complete audit trail. Actions are also explained. Where many service providers remain in Black box mode, which is impossible to explain, we have chosen to be totally transparent and explainable in "Glass Box" mode. Glass Box "mode, thanks to ourAugmented Intelligence. Users can export reports, or individual sheets, to prove that the required due diligence has been carried out.
APScan is an all-in-one tool that can operate in stand-alone mode, and be used by non-expert users. The solution can be fully connected to your Information System (IS) via our APIs, or operate in hybrid mode with simultaneous use of our APIs and our Web Portal.
APScan with over 70 parameter criteria, enables you to configure the tool according to your Compliance policy and risk appetite. APScan is available from anywhere in the world (all you need is an Internet connection) and is available in several languages(FR, EN, ES), with other languages available on request.
APScan complies with all regulations GDPR (*), CyberSecurity is at the heart of our concerns. APScan carries out annual security/intrusion tests orchestrated by recognized independent companies. Today, no security constraint has stood in our way. Numerous security-requiring professions and companies of all sizes already place their trust in us, including major groups known for their zero-risk approach, such as BNPP, BPCE, BPI, Sodexo... Technologically, our API is designed using the latest market standards: Web Service in REST/JSON format, with a secure OAUTH2 authentication system (Bearer Token). The no-code feature enables you to evaluate the full power of our solutions simply and in real time. Our solutions feature an ultra-complete security system: Secure data transfers through https encryption with certificate, segregation of spaces by an application China wall, non-reversible password storage / Encryption of attached documents / Regular data backups (main and backup servers) / Data located and backed up in France / PCA / PRA ... We ensure the integrity, confidentiality and traceability of content throughout the process, from capture to long-term preservation of information. (*) GDPR The acronym GDPR stands for General Data Protection Regulation (GDPR). GDPR provides a framework for the processing of personal data within the European Union. The legal context is adapting to keep pace with changes in technology and our societies (increased use of digital technology, development of online commerce...).
AP Solutions IO delivers a new version of the application every 4 months. Thanks to the SaaS* mode, you automatically benefit from these upgrades without any action on your part. AP Solutions IO takes care of everything, and it's included in the subscription. We're always ready to listen to your specific needs. (*) Saas: Software as a Serviceis a distribution model for IT applications in which a third-party provider hosts the applications and makes them available to customers via the Internet.
Yes, list management is of course controlled by the supervisory authorities:
- In terms of the perimeter used,
- Update frequency,
- Time for re-screening relationship entries (EER) and customer portfolio.
In addition to the search engine, the entire compliance system is audited by the regulators. This must be fully aligned with the company's "theoretical" compliance policy, hence the need for a flexible, configurable tool... But above all, precise and complete traceability and explicability.